Attackers use Cloudflare Tunnel to proxy into victim networks
4.8 (350) · € 34.50 · Auf Lager


PDF) DoH Tunneling Detection System For Enterprise Network Using Deep Learning Technique
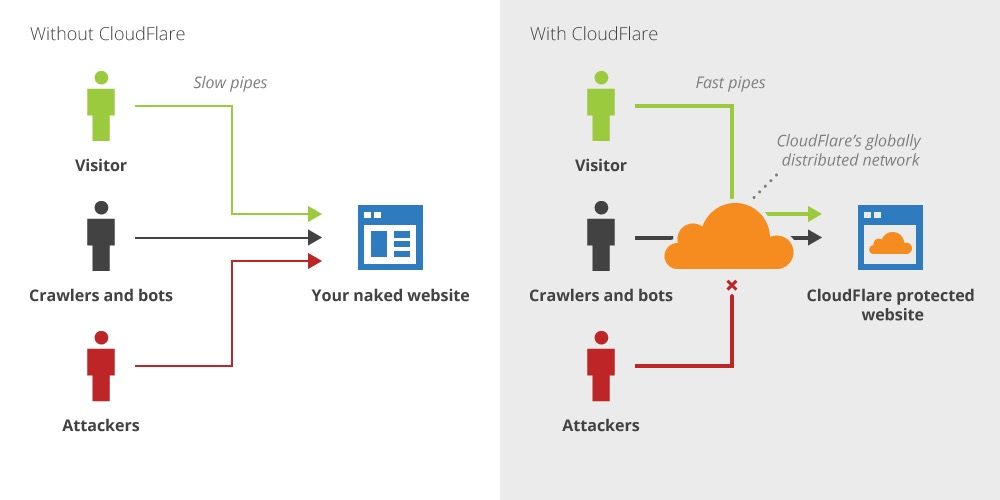
Leveraging Cloudflare Workers to prevent attackers from bypassing your Cloudflare WAF –
Securely access home network with Cloudflare Tunnel and WARP
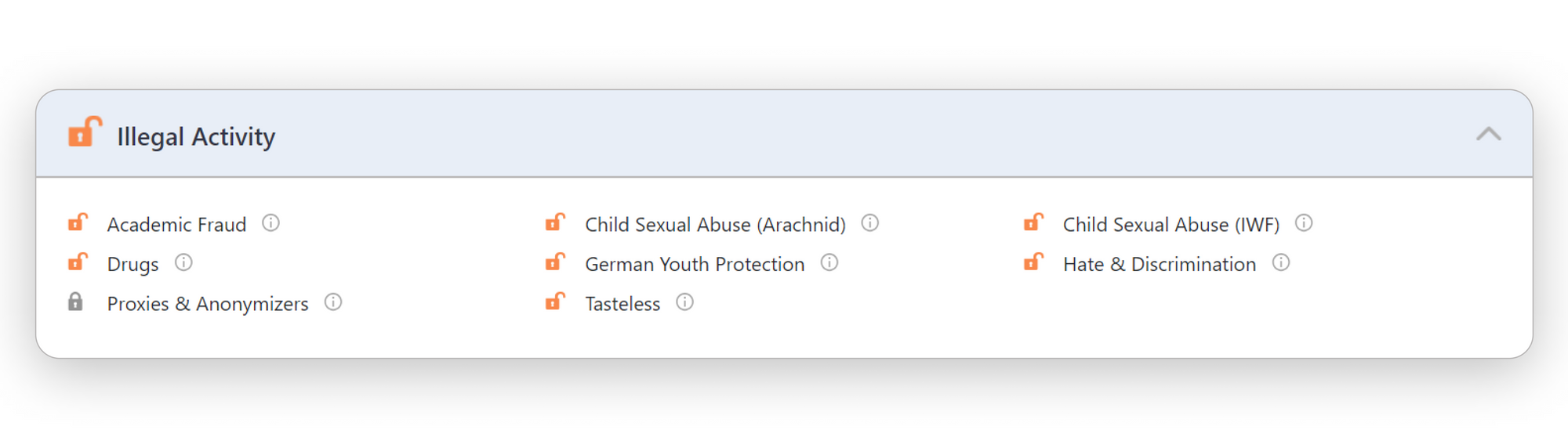
Filtering Bypass and How SafeDNS Can Keep You Secure

Sami Yousef - Secure your network with Cloudflare Tunnels
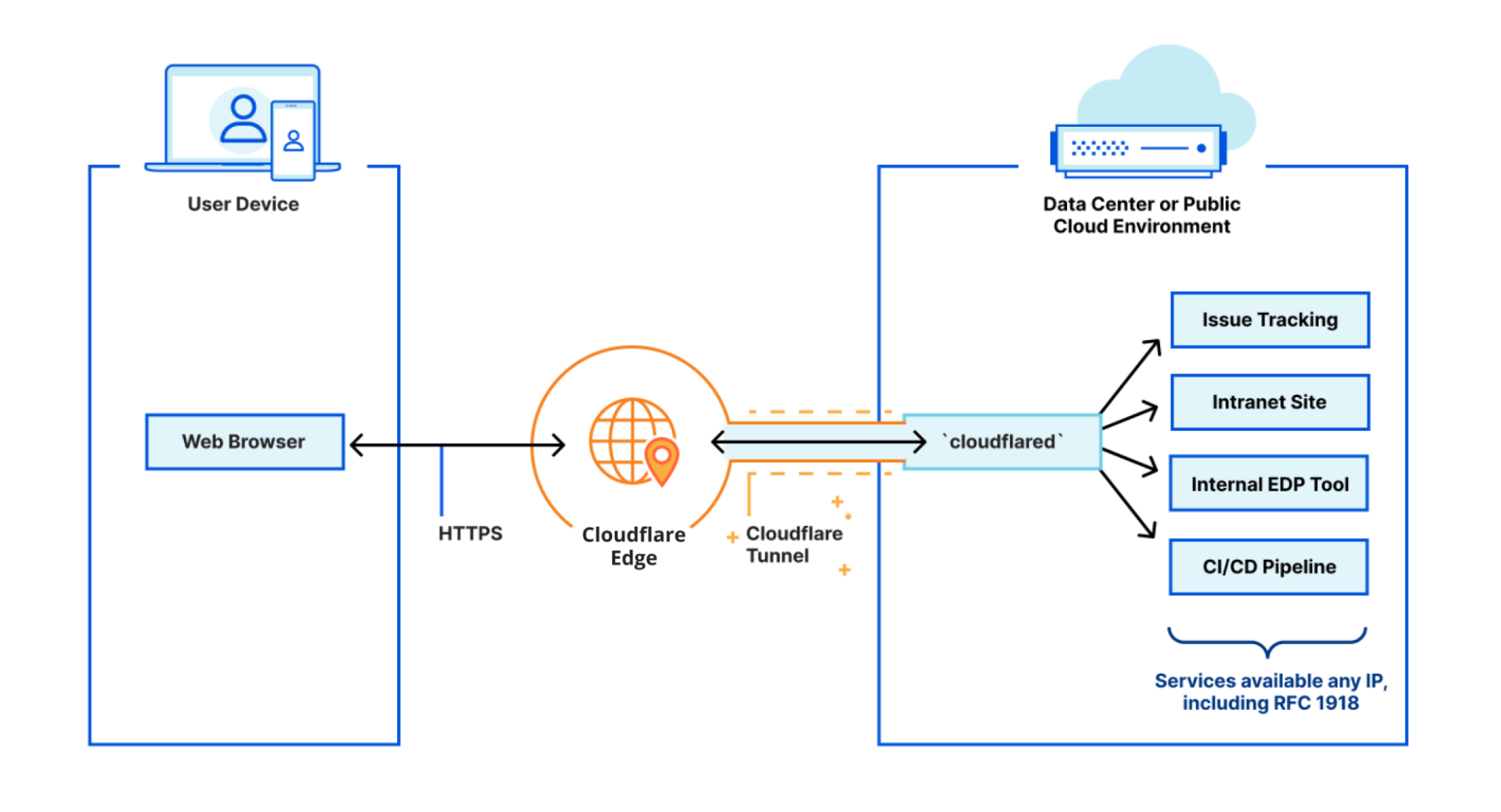
The Zero Trust platform built for speed
New Zardoor backdoor used in long-term cyber espionage operation targeting an Islamic organization

Zero trust tunnel public hostname disable force https proxy redirect - Cloudflare Tunnel - Cloudflare Community
Cloudflare - Loud Canvas Media

Hackers Abuse Cloudflare Tunnels to Gain Stealthy Access
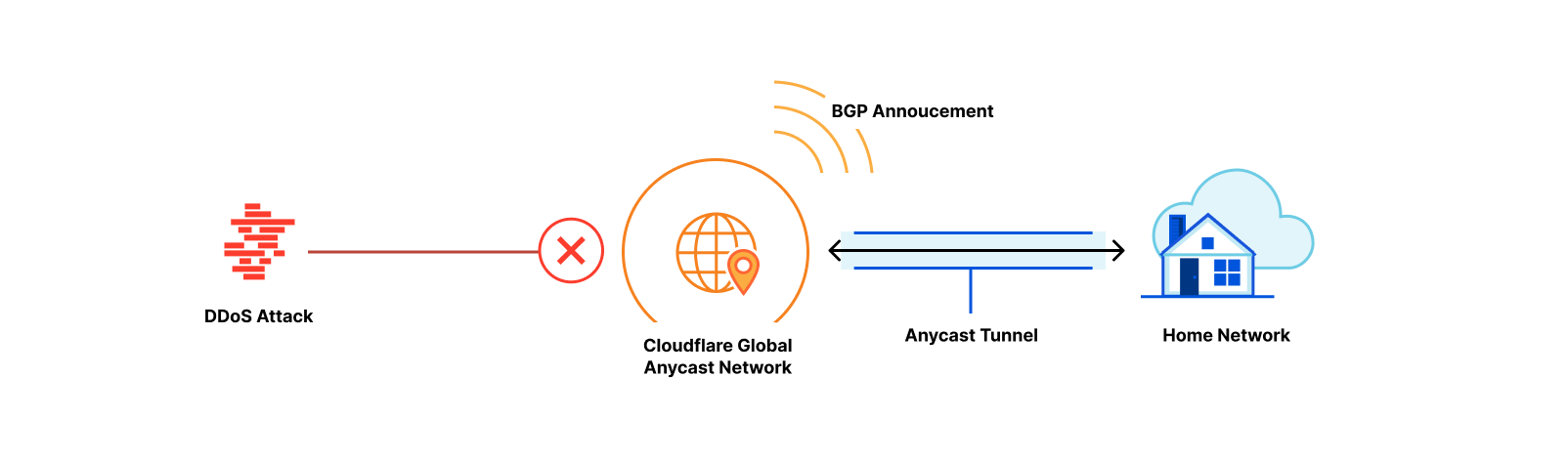
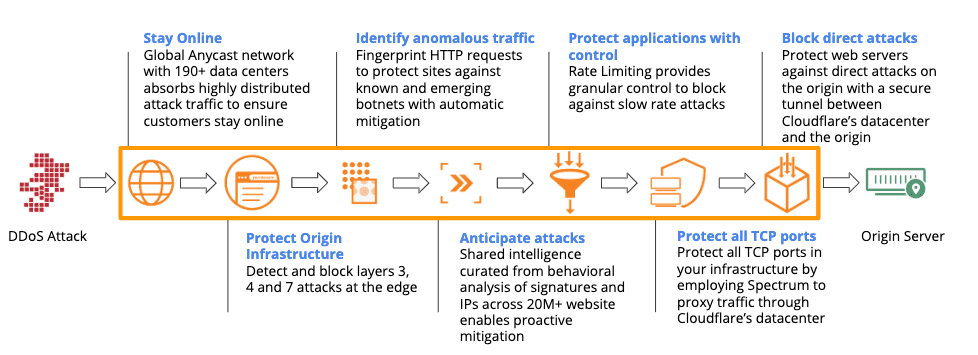
Protect all network traffic with Cloudflare
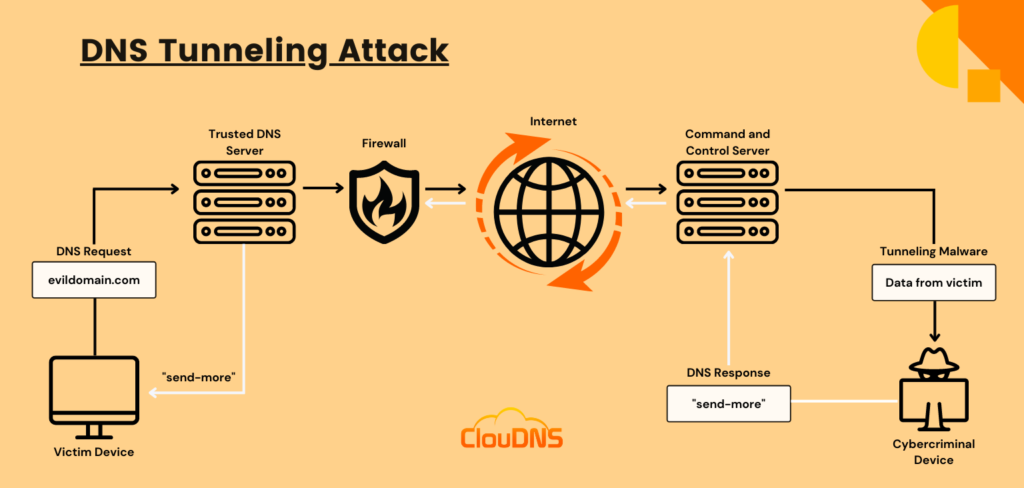
DNS Tunneling attack - What is it, and how to protect ourselves? - ClouDNS Blog
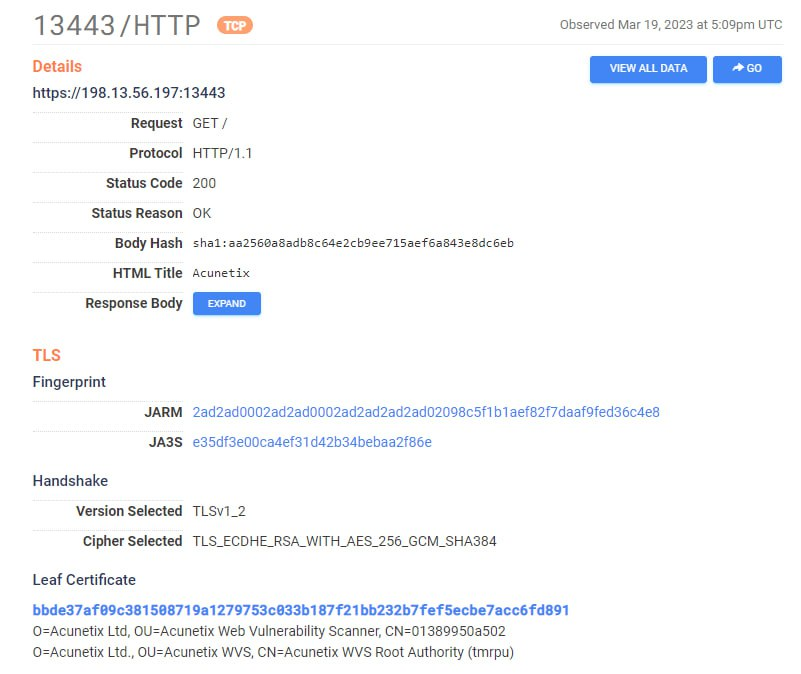
Space Pirates: a look into the group's unconventional techniques, new attack vectors, and tools







